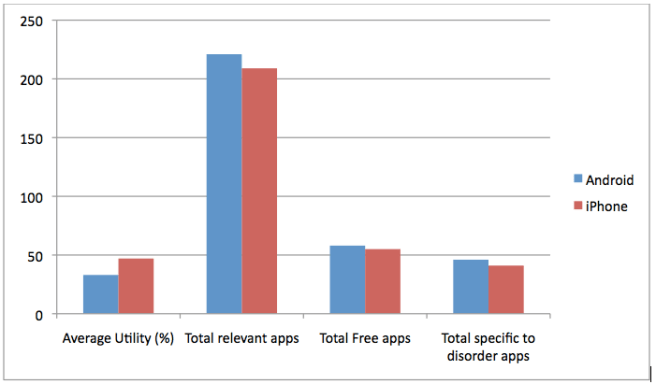
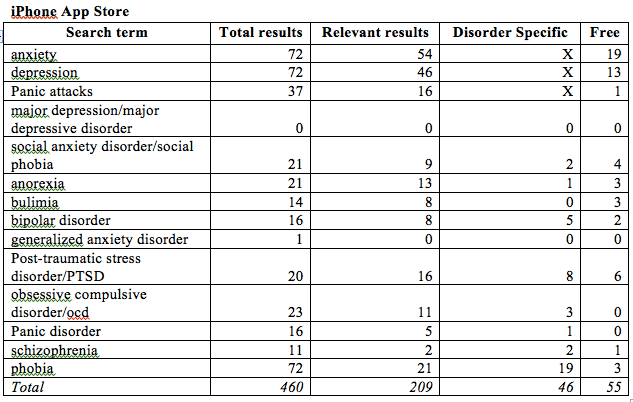
With the appliancization of the Internet, more and more consumers are accessing the web using a variety of non-browser based applications. Because the applications are built for specific platforms, the shift to apps gives more power to the owners of the platforms. Developers have to choose whether to build their apps for Android, Apple, Windows or a combination of the options.
So far, Apple has been falling out of favor among developers. With its much tighter restriction on which App gets approved, Apple is losing to the Android operating system where developers enjoy more freedom in designing their programs. As Windows mobile platform starts to pick market share, Apple might fall further since Microsoft plans to sets its restrictions on app distribution and approval process somewhere between that of Android and Apple.
In 2009, Google filed a complaint against Apple for rejecting its Google Voice app, citing the decision as outrageous and requesting FCC to investigate. Another bad press for Apple was when it rejected Google Latitude on the ground there was already another map app on iPhone, and it would be confusing for users to have two. Despite the negative PR, theoretically Apple should be allowed to choose whichever program it permits on its platform. Some would argue that Apple is just like a supermarket that provides platform for products, such as fruit and vegetables. The supermarket reserves the right to decide which products it takes on, and Apple should be allowed to do the same with apps from developers.

However, the fundamental difference between Apple’s platform and a supermarket is that unlike the supermarket, Apple does not purchase the apps from developers. Instead, it takes a 30% cut on the revenue generated by the program. Though Apple still has the right to decide who to partner with, it should not just arbitrarily decide which app to reject. Often the decision standard Apple uses becomes controversial, and its practices reflect excessive protection of the App Store revenue model. Earlier this year, Apple rejected a few apps that used Dropbox, because once a user is in Safari in the “Desktop Version”, it was possible for him to directly purchase additional space from the website without going through Apple’s App Store. This violated the App Store Review Guidelines that outlaw Apps using a system other than the Apple’s In App Purchase API to buy services. Dropbox saved developer’s apps by getting rid of its “create account” option in one of its APIs. However, it seems Apple is simply getting too much control over what external links can be referenced in an app.

Unfortunately, developers are losing in the battle in software distribution as well. Instead of the freedom of software distribution spreading to App stores, we are experiencing the opposite. A Forbes article compared the new distribution model to the Hollywood studio model where a few large companies, such as Warner Brothers, are in control of all the distribution. Just as Paramount and Columbia Pictures decide most all movies’ distributions, we will have Apple, Google and Microsoft deciding the fate of software. Apple gained additional leverage by introducing the Sandboxing requirement. Apps will have to be Sandboxed before introduced to the Mac App Store, and through the process Apple will have the power to determine whether to restrict certain resource access of the Apps. Software programs will be completely at Apple’s mercy in term of whether it could access internet, networking or write access.

As appliancization continues, platform and app store providers will act as the Gate Keeper to check for security issue, copyright violations and other regulations. App and software developers will lose more and more freedom as they become increasingly reliant on the distribution functions of Apple, Google and Microsoft. Unless developers rise up and revolt against Apple’s control, the Gate Keeper’s restrictions will dampen creativity, freedom of speech and innovation.
Additional Resources:
http://www.forbes.com/sites/rogerkay/2011/11/04/apples-mac-os-lockdown-to-end-developer-independence/
http://thenextweb.com/google/2012/11/13/google-declares-flash-is-now-fully-sandboxed-in-chrome-for-windows-mac-linux-and-chrome-os/
http://www.nationalreview.com/agenda/244145/chris-anderson-appliancization-internet-reihan-salam#
http://www.businessinsider.com/iphone-app-rejections-2009-12#google-voice–latitude-7